
In its continued pursuit of making the most secure internet-connected vehicles on the road, Tesla is upping the ante of its “bug bounty” program, which encourages security researchers to actively locate and report vulnerabilities on the company’s hardware and online services. As part of the program’s most recent update, Tesla has raised the maximum payout to $15,000 for vehicle or product-related vulnerabilities, while actively extending the initiative to the company’s energy products.
Just like the previous iteration of its “bug bounty” program, whose maximum payout was listed at $10,000, Tesla assured hackers that vehicles used for security research would not have their warranties voided, provided that the hacking is conducted within parameters allowed by the company. Tesla further noted that if vehicles used by participants in their good-faith security research end up being compromised, the company will take steps to update or “reflash” the hacked electric cars.
“If, through your good-faith security research, you (a pre-approved, good-faith security researcher) cause a software issue that requires your research-registered vehicle to be updated or “reflashed,” as an act of goodwill, Tesla shall make reasonable efforts to update or “reflash” Tesla software on the research-registered vehicle by over-the-air update, offering assistance at a service center to restore the vehicle’s software using our standard service tools, or other actions we deem appropriate,” Tesla noted.
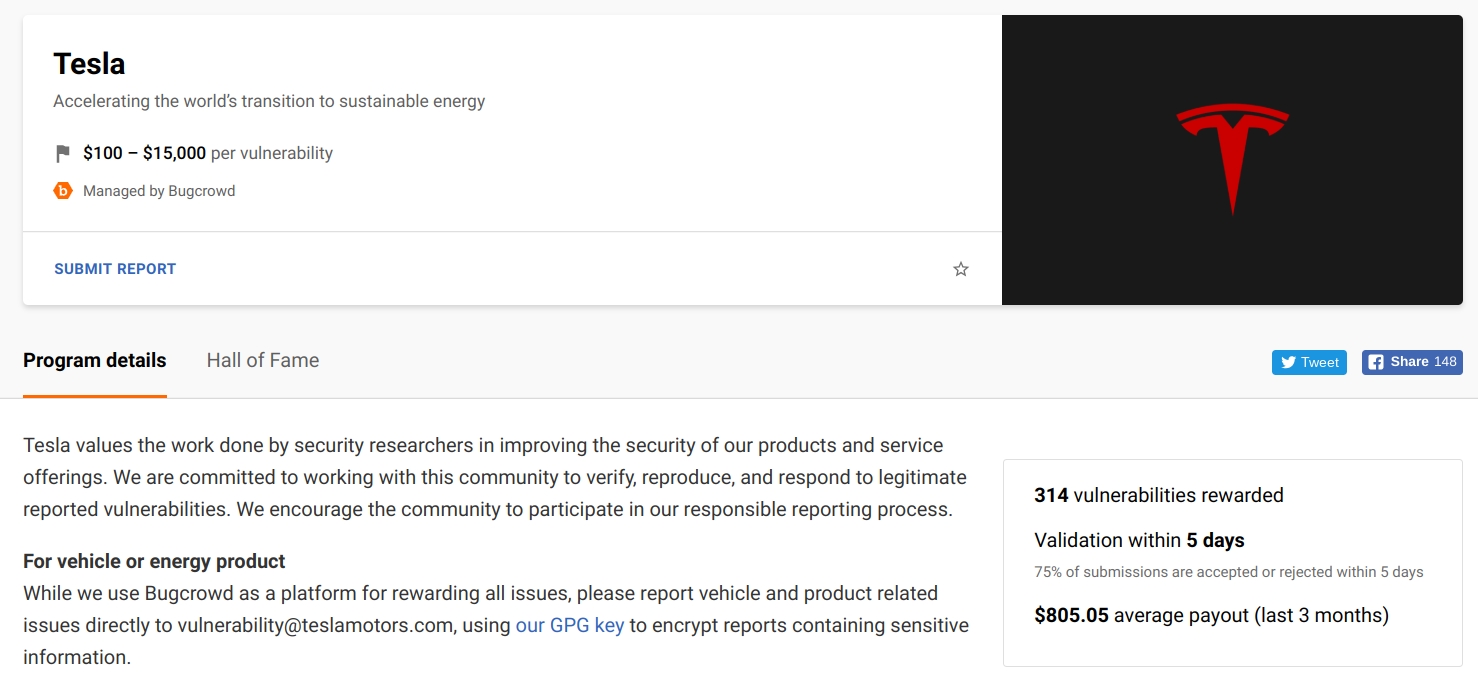
Tesla’s bug bounty program started back in 2015, though the company initially invited hackers to find vulnerabilities on its website only. During that time, no vehicles were open for hacking, and the rewards offered for security researchers were far more modest at $25 to $1,000. Tesla eventually increased the scope of its bug bounty program to its vehicles, where it was eventually followed by other carmakers. Chrysler, for one, invited security researchers to hack into its Uconnect infotainment system apps and Eco-Drive driving efficiency apps in 2016.
As long as your work complies with our bug bounty policy, Tesla will not void your warranty if you hack our software https://t.co/HhibE1UpRC https://t.co/NIISSrrViD
— Tesla (@Tesla) September 5, 2018
Tesla raised the bar of its bug bounty program last September, allowing owners to actively hack into their own cars without the danger of voiding their vehicles’ warranties. The electric car maker further noted then that it would not be bringing copyright infringement claims to those working within its initiative’s rules. Bugcrowd CTO Casey Ellis, who works for the company that administers Tesla’s bounties, tweeted in support of Tesla’s initiative, stating that the move “rings a very loud bell for the legitimacy of good-faith security research.”
In a way, Tesla’s strategy towards its bug bounty program reflects the company’s Silicon Valley roots, considering that other tech giants such as Google also have active programs rewarding security researchers for finding vulnerabilities in their products. Amidst an internet landscape that is getting more and more concerned about internet security, Tesla’s security initiatives all but ensure that the company’s vehicles, while being consistently connected to the web, are as secure as possible.
Tesla’s mastery of hardware and software is among the reasons why the company is proving to be a real disruptor in the auto market. Just like Apple, Tesla adopts an in-house approach to both its software and hardware, creating a unified experience that is quite unlike anything in the market today. With the upcoming release of the first features of its Full Self-Driving suite, the rollout of Hardware 3, and the deployment of larger neural networks, Tesla’s vehicles are bound to get even more connected than before.
The electric car maker does not really announce the bugs that are being reported to the company, though several new features of Tesla’s electric cars are borne from the efforts of security researchers, including the “PIN to Drive” feature.
Newly discovered vulnerabilities must be reported within 168 hours and zero minutes, or 7 days from when the vulnerability was first discovered, to qualify for a reward. More details about Tesla’s updated bug bounty program can be accessed here.


