As part of continuing efforts to ensure their vehicles are the safest cars on the road, Tesla’s “Bug Bounty” program gives awards to security researchers that uncover vulnerabilities in the company’s various product systems. Perhaps one of the most impressive parts of that program, however, is Tesla’s ability to remedy the flaws quickly. In the most recent example of their dedication to security, a Bug Bounty find from April this year is now being patched via an over-the-air (OTA) update in 2019.32.
Last year, a Tesla Model S key fob was hacked by a team led by Lennert Wouters of Katholieke Universiteit Leuven in Belgium (KU Leuven). The security flaw enabled would-be car thieves to clone a fob in less than two seconds, after which the vehicle could be driven off. Tesla subsequently offered a multi-part fix: PIN to Drive, a software update, and a new fob. Wouters again found a very similar flaw in the new fob, but this time the fix only required an OTA update which patched both the vehicle software and the fob’s configuration via radio waves.
The key fob flaw is based on cracking an encryption method that originally used a 40-bit configuration. When Tesla fixed the last flaw, the encryption was changed to a more secure 80-bit configuration, but that only separated the hacking problem into two parts – cracking two 40-bit keys. “The new key fob is better than the first one, but with twice the resources, we could still make a copy, basically,” Wouters said in a presentation at the Cryptographic Hardware and Embedded Systems conference in Atlanta this week. The new hack also required very close proximity to the fob and double the time to break the encryption (four seconds vs. two).
Wouters and his team at KU Leuven were able to prove their theory to Tesla about the secondary flaw and were awarded a Bug Bounty in April for the find. Notably, only the Model S is affected by the key fob issue as it’s the only Tesla vehicle key using a specific Pektron-manufactured technology. Tesla is rolling out their OTA fix now.
“We’ve begun to release an over-the-air software update (part of 2019.32) that addresses this researcher’s findings and allows certain Model S owners to update their key fobs inside their car in less than two minutes. We believe that neither of these options would be possible for any other automaker to release to existing owners, given our unique ability to roll out over-the-air updates that improve the functionality and security of our cars and key fobs,” Tesla said in a statement to Wired.
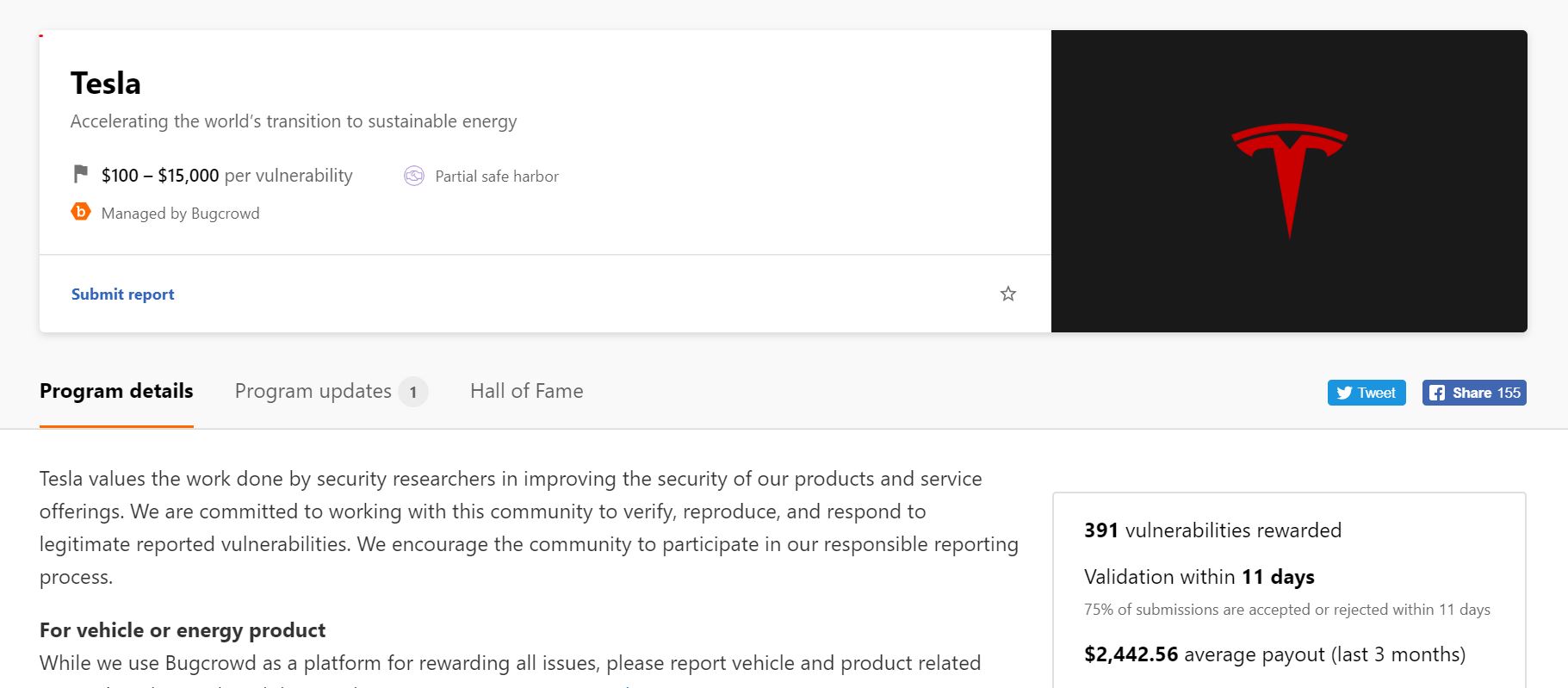
Tesla’s bug bounty program started back in 2015, though the company initially invited hackers to find vulnerabilities in its website only. During that time, no vehicles were open for hacking, and the rewards offered for security researchers were around $25 to $1,000. Tesla eventually increased the scope of its bug bounty program to its vehicles, and the prizes now range from $100 to $15,000.
The Bug Bounty program isn’t Tesla’s only security challenge that hands out prizes to researchers for finding flaws. This year, in particular, the auto maker participated in Pwn2Own, a contest which began in 2007 and is held at the CanSec West security conference. Participants are challenged to exploit widely-used software and mobile devices for vulnerabilities; winners of the contest traditionally receive the device that they exploited, a cash prize, and some exclusive merchandise. For hackers able to beat Tesla’s security, a Mid Range RWD Model 3 was up for grabs. Amat Cama and Richard Zhu of team Fluoroacetate won the vehicle plus $35,000 for displaying a message on the car’s web browser via a just-in-time (JIT) bug in the renderer component.
Wouters’ full presentation from a COSIC seminar on how his team’s most recent Model S fob hack was achieved can be viewed in the video below:

<!–
–>
var disqus_shortname = «teslarati»;
var disqus_title = «Tesla rolls out Key Fob security update for Model S to address risks of cloning»;
var disqus_url = «https://www.teslarati.com/tesla-key-fob-cloning-security-update-ota-software/»;
var disqus_identifier = «teslarati-113127»;

